2024-10-17
The Role of Images in Capture the Flag Challenges
In many Capture the Flag (CTF) competitions, images play a crucial role in various challenges. While images like PNG, JPG, or GIF files might appear as simple visuals, they often hide critical information. Whether it's hidden metadata, manipulated file headers, or embedded content, images can be tricky yet fascinating puzzle pieces in CTF challenges.
How Images are Used in CTF Challenges
Images in CTFs often contain hidden data or clues that participants must extract to find a flag. Here are some common techniques used to hide information within images:
1. Metadata Hiding
Many image files, such as PNGs and JPGs, contain metadata—information about the file itself, including the camera used, the date it was taken, or even geolocation data. In CTF challenges, this metadata can sometimes hold a hidden flag or clue.
To inspect an image’s metadata, tools like exiftool or strings are commonly used:
exiftool image.png- Extracts metadata from the image.strings image.png- Displays all readable strings inside the image file.
2. Steganography
Steganography is the practice of hiding messages or data within a file in a way that doesn’t alter the file's appearance. In CTF challenges, an image may contain hidden text or flags encoded in the least significant bits (LSB) of its pixels, which are imperceptible to the naked eye.
Tools like Steghide or zsteg can be used to extract hidden data:
- Steghide: Can hide and extract data from images or audio files.
- zsteg: Specialized for PNG files, it helps detect LSB steganography.
3. Hidden Data in File Headers
An image’s file header contains important information about the file type and structure. In some CTF challenges, images may have deliberately altered or confusing headers that prevent them from opening properly or obscure their true nature. For example:
- A file that appears to be a .jpg may actually be a .zip archive if the file header is modified.
- Changing the file extension might help you reveal the hidden contents.
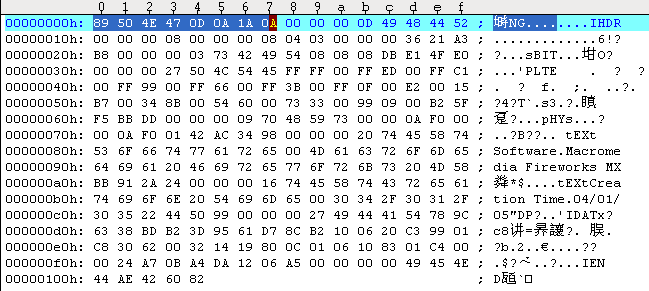
To analyze or repair such headers, tools like xxd or binwalk can be useful. The xxd command converts a file to its hexadecimal representation, making it easier to identify if the file type has been altered.
4. Embedded Files
Sometimes, an image file may contain additional embedded files (e.g., a ZIP or PDF) hidden within it. These can be extracted by using forensic tools like binwalk:
binwalk -e image.png- Scans and extracts embedded files from the image.
In such cases, a flag may be hidden inside the embedded content, and your task is to extract and analyze it.
Common Tools for Image-based CTF Challenges
| Tool | Description |
|---|---|
| exiftool | Extracts metadata from images and other file types. |
| strings | Shows readable strings inside a file. |
| Steghide | Hides or extracts data from image or audio files. |
| zsteg | Detects steganography in PNG files. |
| binwalk | Scans and extracts hidden or embedded files. |
| xxd | Converts a file to hexadecimal for manual inspection. |
Example: A PNG Challenge
Consider a CTF challenge where you are provided with a seemingly normal PNG file, but the flag is hidden inside it. Here’s how you might approach it:
Step 1: Check Metadata First, you can inspect the file's metadata using
exiftool:exiftool suspicious_image.pngIf the flag is hidden in the metadata fields, it will appear in the output.
Step 2: Extract Hidden Data If no flag is found in the metadata, use
Steghideorzstegto detect hidden steganographic data:zsteg suspicious_image.pngStep 3: Analyze the File Structure If the image still doesn’t yield any results, you can try
binwalkto check for hidden embedded files:binwalk -e suspicious_image.png
By systematically applying these techniques, you can uncover hidden flags buried within seemingly simple image files.
Conclusion
Images are more than what they seem in CTF challenges. From metadata and steganography to embedded files and manipulated headers, they often hide valuable clues that can lead to capturing the flag. Having a solid understanding of how to inspect and analyze images with the right tools is essential for any CTF participant.
By mastering techniques like metadata extraction, steganography, and file header analysis, you’ll be well-equipped to tackle any image-based challenge in a CTF competition. Happy hacking!